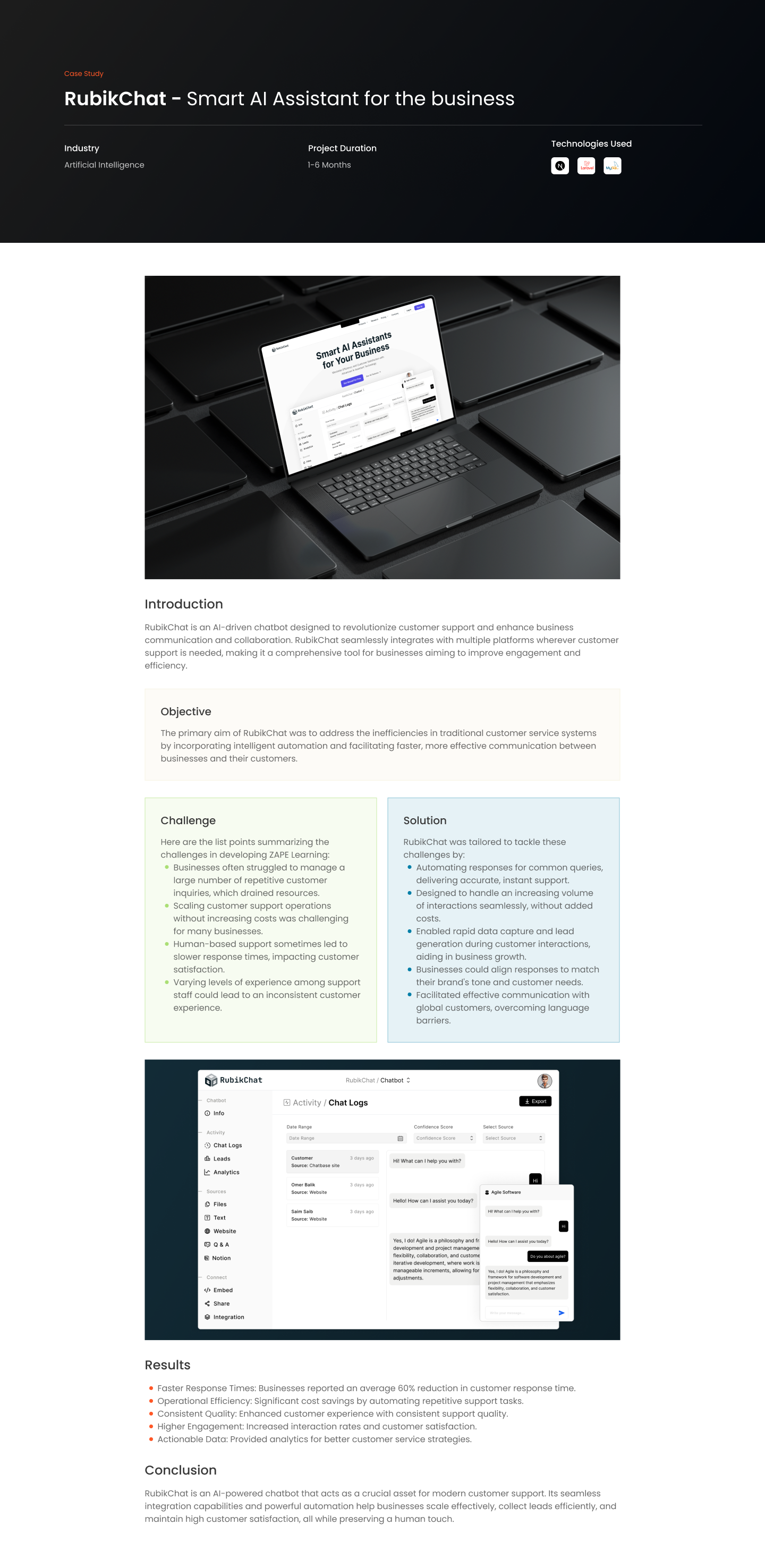
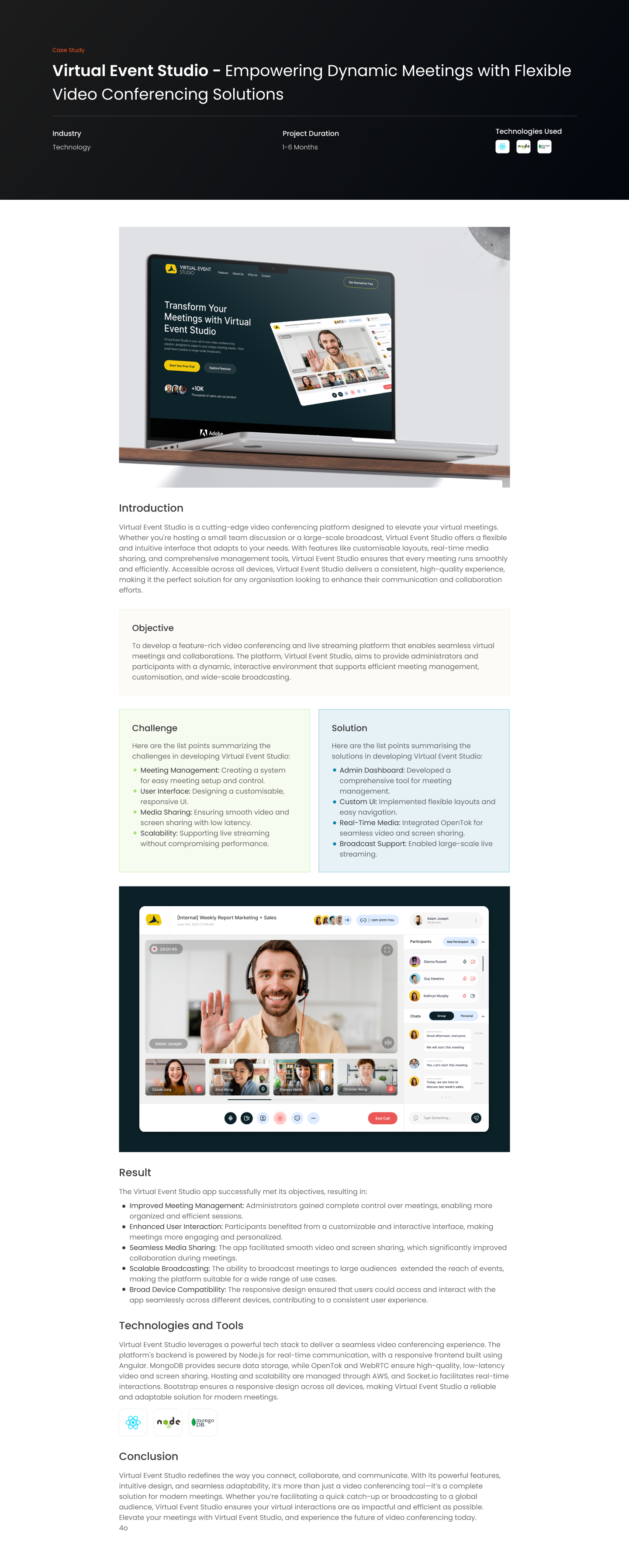
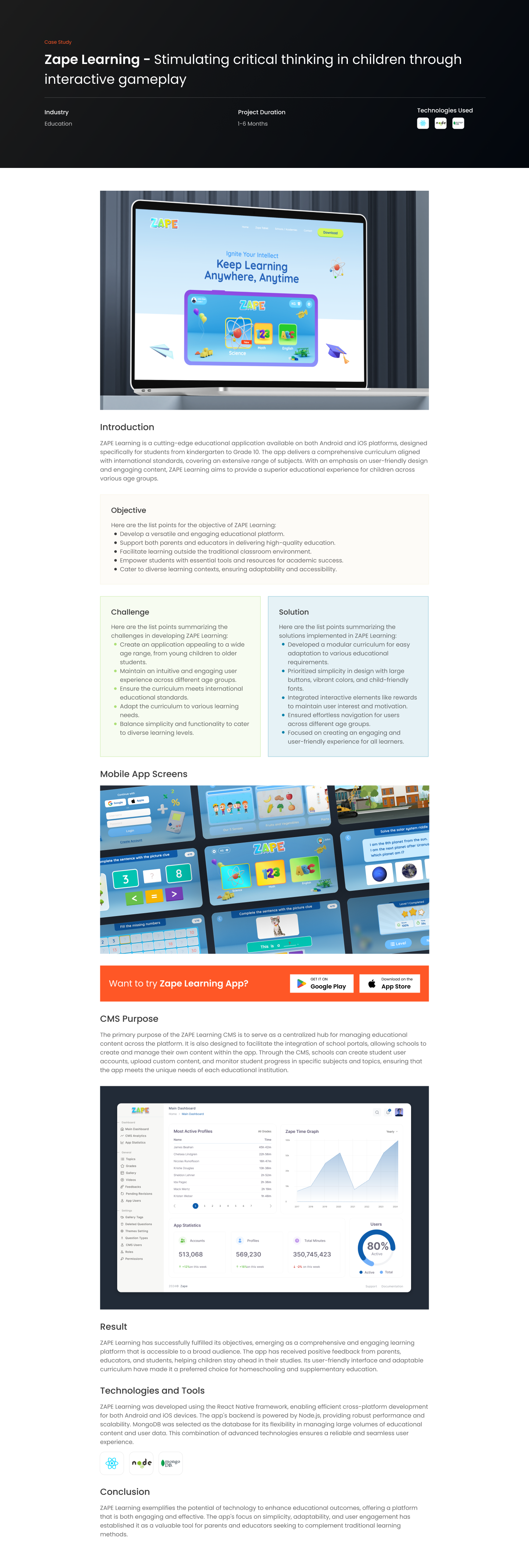
In today’s digital landscape, web applications serve as crucial platforms for everything from
communication and online shopping to information dissemination. Given this growing dependency, the importance of cybersecurity has never been more critical.
Implementing robust security measures is essential for protecting sensitive data and ensuring a
safe user experience. Below are key cybersecurity best practices that developers and organizations should integrate into their web application development and maintenance processes.
HTTPS ENCRYPTION:
Leverage HTTPS to ensure the integrity, confidentiality, and authenticity of the data transmitted between users and the web application. This goes beyond mere encryption and offers a secure channel of communication, protecting against eavesdropping and data tampering.
INPUT VALIDATION AND SANITIZATION:
Introduce stringent input validation and sanitization mechanisms to defend against injection attacks such as SQL injection and cross-site scripting (XSS).
AUTHENTICATION AND AUTHORIZATION:
Utilize robust authentication methods, including multi-factor authentication (MFA), and apply strict authorization controls to define appropriate access levels for users.
SESSION MANAGEMENT:
Adhere to secure session handling protocols, incorporating features like session timeout and token regeneration. Invalidate sessions after logout or prolonged periods of inactivity.
CSRF AND XSS PROTECTION:
Guard against Cross-Site Request Forgery (CSRF) and Cross-Site Scripting (XSS) by using anti-CSRF tokens and sanitizing user inputs.
HTTP SECURITY HEADERS:
Employ HTTP security headers such as X-Content-Type-Options, X-Frame-Options, and X-XSS-Protection to fortify your application against potential threats.
FILE UPLOAD SECURITY:
Manage file uploads securely by restricting file types and sizes. Perform thorough validation on uploaded files to minimize vulnerabilities and the risk of malware injection.
SECURE CODING PRACTICES:
Follow secure coding standards and regularly carry out code reviews to identify and fix security vulnerabilities during the development cycle.
ERROR HANDLING AND LOGGING:
Execute proper error handling mechanisms to limit the exposure of sensitive information. Maintain secure logs and monitoring systems to swiftly detect and respond to security incidents.
REGULAR SECURITY TESTING:
Engage in frequent security testing activities, which include penetration testing and vulnerability scanning, to proactively identify and rectify security weaknesses.
DATABASE SECURITY:
Implement robust access controls and encryption techniques for sensitive data stored in databases. Keep your database system updated and patched to fend off potential security threats.
API SECURITY:
APIs often serve as an entry point for attackers; therefore, secure them using measures like OAuth tokens and data validation.
FIREWALLS:
Incorporate firewalls to filter out malicious traffic and protect your web application from unauthorized access.
INCIDENT RESPONSE PLAN:
Develop a comprehensive incident response plan that outlines the steps to take in the event of a security breach, ensuring a quick and effective resolution.
SECURITY EDUCATION AND TRAINING:
Foster a security-conscious culture by educating and training all stakeholders—developers, administrators, and end-users—about security best practices and potential cyber threats.
By embedding these cybersecurity best practices into your web application development and
maintenance, you’re taking a vital step toward safeguarding against evolving cyber threats and ensuring a secure and reliable user experience.